By utilizing the power of graphical processing units and partnering with Netriver, Wordfence can simulate a password cracking attempt using a library that contains more than 260 million passwords.
The library is made up of previous hacks on major websites and services. For example, if your password was leaked during the LinkdIn hack in 2012, Wordfence will inform you that it’s no longer safe to use.

I audited the passwords of all users on the Tavern test site and no weak passwords were discovered. I changed my password to password and within seconds, Wordfence detected a weak password.
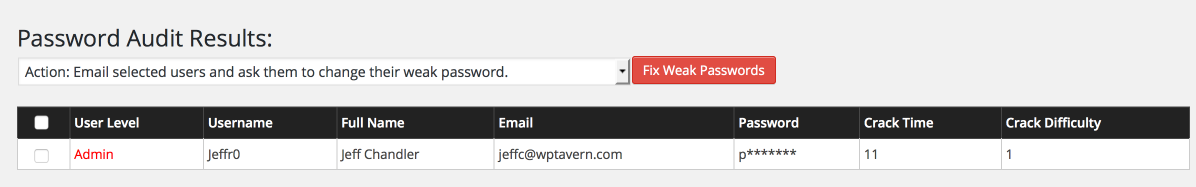
When a weak password is detected, you can email selected users and request that they change it to a strong one. Alternatively, you can let Wordfence change it to a strong one automatically and email it to the user.
Wordfence explains how the auditing process works.
Internally this feature uses a double layer of encryption to protect your data during the audit. First, we encrypt the hashes we are going to operate on using a combination of AES encryption and RSA public key encryption.
Then we send your encrypted data via SSL to our servers which provides a second layer of encryption. Once on our servers, the data is stored encrypted until it is audited and we never return sensitive data to your website.
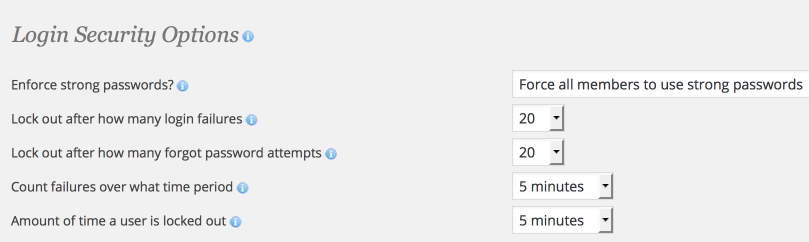
Although WordPress 3.7 added an improved password strength meter, WordPress doesn’t enforce password strength for new users. After performing an audit, I recommend turning on the option in Wordfence to enforce strong passwords for new users. This way, you’ll know that all passwords from that point forward are strong.
Earlier this year, SplashRiver released its list of the 25 worst passwords used in 2014. The passwords include, 123456, password, and 12345. Password auditing in Wordfence is a convenient way to make sure none of the users on your site are using weak passwords like those in the report.
Hah! In other words you’re giving Wordfence permission to bruteforce your passwords. Nice. And then the next version might ship with a shell for them to control your server, but hey that’s for your security and don’t worry, it’s encrypted. No thanks :)