WordPress 3.7 is right around the corner with the beta out this weekend and the official release coming in mid-October. This release has a strong focus on improving WordPress security and includes automatic updates to help installs stay up to date with maintenance and security releases. If you install the beta and have a play, you’ll find some fancy, yet subtle changes under the hood.
WordPress 3.7 Helps New Users Make Better Password Decisions
Have you ever wondered whether or not password strength meters help anyone? They’re employed on nearly every website with user capabilities, including WordPress sites, which account for a large chunk of the web.
Password strength meters can help users select stronger passwords but only if the script the meter uses to estimate password strength is helpful. That’s why WordPress 3.7 will be making use of Dropbox’s zxcvbn library.
A cursory test of the new password meter in WordPress reveals that it is stricter in what it considers to be a strong password.
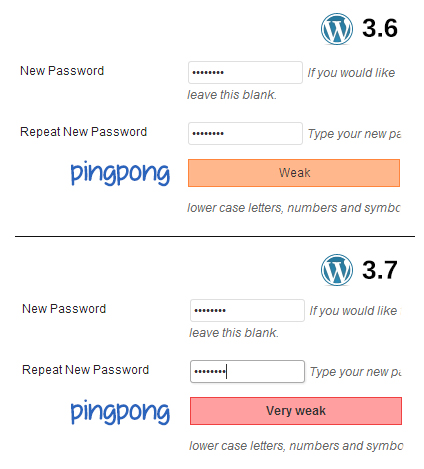
But the new password strength meter goes far beyond simply being “stricter” and is actually much smarter in how it performs its estimations.
Smarter Password Strength Estimations
The challenge of creating passwords that are easy for you to remember, yet difficult for hackers to crack, led to the common practice of l33t speak substitutions, ie. using 3 for e, 0 for o, etc. However, this practice is so common now that it’s quite easy for these kinds of passwords to be cracked. Nevertheless, password meters are still ranking these passwords as strong because they contain a combination of letters, numbers and symbols.
The zxcvbn library actually accounts for this and therefore its evaluation is not merely stricter but rather, it’s a smarter estimation of password strength. Whereas “G00dm0rn1ng!” may have previously been considered a strong password in WordPress 3.6, the new password meter rates it as being very weak.
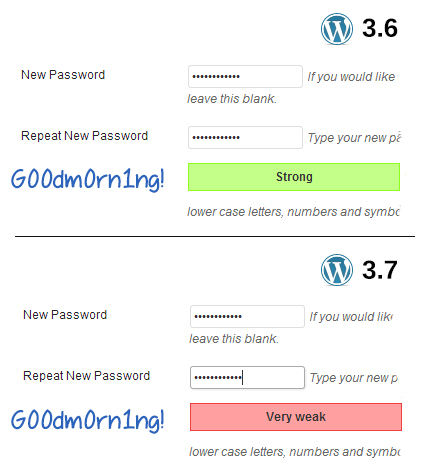
It’s interesting to note that “G00dm0rn1ng!” scores very well on a password scoring checklist, but due to its common number/letter substitutions, it would not be considered a strong password by WordPress 3.7’s new password meter.
How does it perform better calculations? Well, this is a matter of some major geekery. zxcvbn first performs a match to see if the password entered matches against common passwords and patterns that are easy to crack. Currently it matches against:
- Several dictionaries (English words, names and surnames, Burnett’s 10,000 common passwords)
- Spatial keyboard patterns (QWERTY, Dvorak, and keypad patterns), repeats (aaa), sequences (123, gfedcba), years from 1900 to 2019, and dates (3-13-1997, 13.3.1997, 1331997).
- Recognizes uppercasing and common l33t substitutions for all dictionaries
Secondly, it assigns the password a score based on entropy in bits. Password entropy is calculated by the number of times a space of possible passwords can be cut in half, as outlined by Dan Wheeler in his article explaining zxcvbn’s model of estimating realistic password strength.
zxcvbn calculates a password’s entropy to be the sum of its constituent patterns. Any gaps between matched patterns are treated as brute-force “patterns” that also contribute to the total entropy
This is a simple calculation but without checking for commonly used patterns, older methods of determining password entropy are too simplified to be useful.
Lastly, the search aspect of the model finds the simplest (lowest entropy) non-overlapping sequence after analyzing the possibilities for overlapping matches. It can then give a more accurate estimation of the complexity of the password structure.
All that to say, with the help of zxcvbn, WordPress is giving much more sound password advice to its users in 3.7. It’s important to note that WordPress doesn’t actually force you to use a stronger password. You can still go on using “admin123” if you want to leave all your doors unlocked for hackers. But the new password strength meter in WordPress 3.7 should help users make better decisions.
Obligatory xkcd comic: http://xkcd.com/936/