Last week CloudFlare released the first update to its official WordPress plugin in approximately six months. Although the release post refers to the update as “CloudFlare’s new WordPress plugin,” it is essentially a major rewrite and a jump from version 1.3.25 to 3.0. The previous changelog has been wiped out and replaced with notes for the 3.x releases only.
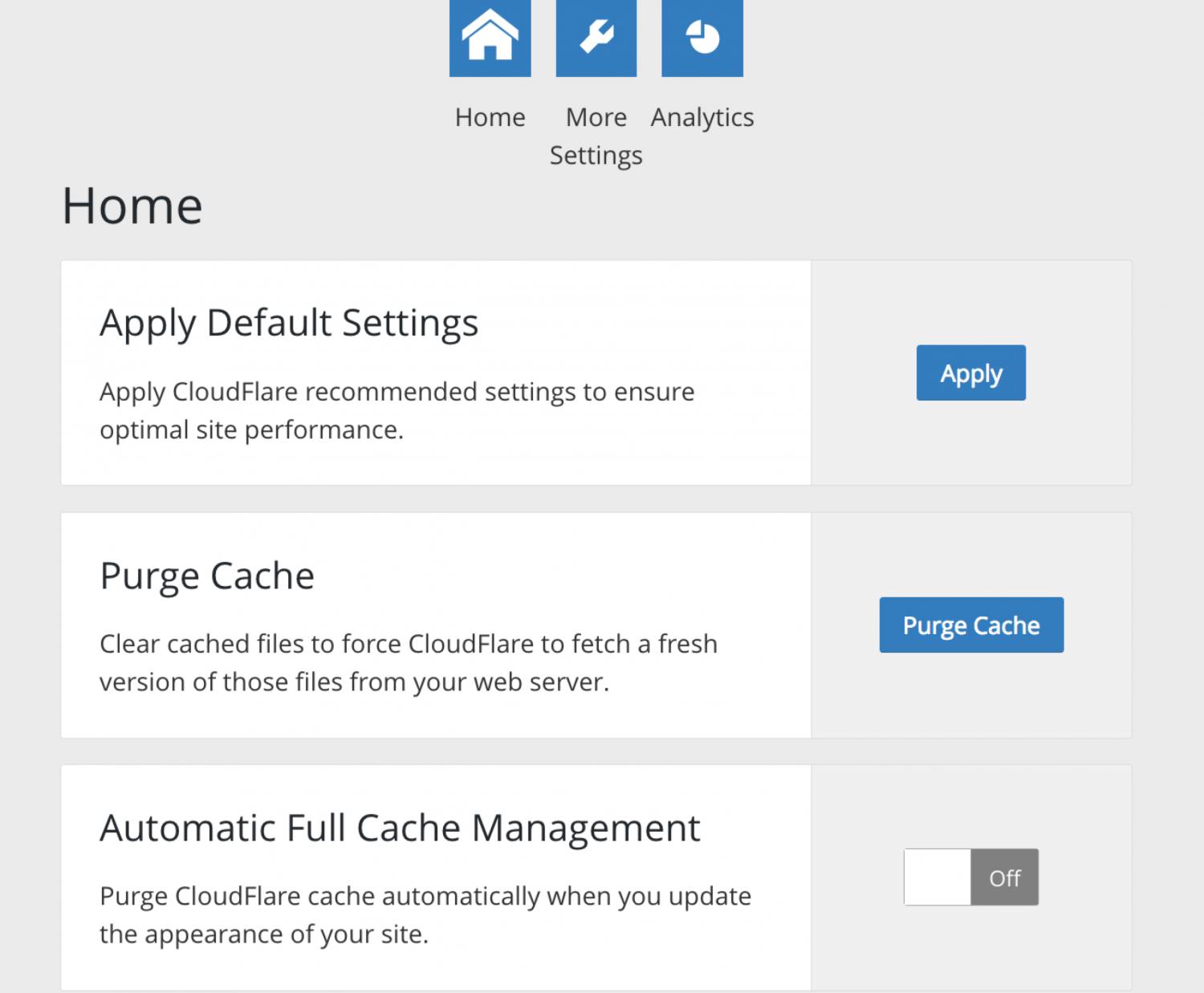
CloudlFlare 3.0 introduces one-click optimized settings for WordPress. These defaults include security set to medium, auto minify for JS, CSS, and HTML, 4-hr cache expiration, and email address obfuscation enabled, among other settings.
The latest update also adds an optional setting for automatic cache purging that will happen in the background when users make changes to the appearance of their websites. This feature hooks into switch_theme and customize_save_after to purge the cache upon theme changes and edits saved from inside WordPress. Users can still manually purge the cache on the settings page.
The “More Settings” page allows users to tweak CloudFlare settings within the WordPress admin, as opposed to navigating to the CloudFlare.com dashboard. Users can also view analytics for total visitors, bandwidth saved, and threats blocked.
CloudFlare 3.0+ adds Web application firewall (WAF) rulesets for users on a commercial plan. The WAF includes rules that mitigate WordPress-specific threats and vulnerabilities.
There are some important changes listed in the plugin’s changelog that CloudFlare neglected to mention in its release post. The 3.0 release removes submission of spam comments as well as the ability to toggle Development Mode on/off.
It also removed HTTPS protocol rewriting and added HTTP2/Server push. After HTTP/2 Server Push led to 520 and 502 errors for some websites, CloudFlare removed it in a subsequent maintenance release (3.0.2). The feature has not yet been re-added to the plugin, but CloudFlare developers are in the process of rewriting it. The plugin’s author explained why users were seeing excessively large headers with the update:
We did a lot of QA on this latest release. It was in beta for about a month with over 55 beta testers. The root cause of the 520 and 502 http error codes was because our implementation of HTTP2/Server push created too many headers for websites with lots of resources to load. We never saw this during testing because by chance none of our beta testers had front ends large enough to trigger the header bug.
Feedback in the plugin’s support forums indicate that many users were unable to log into their sites after the update and unable to configure settings. Other users are reporting mixed content warnings. In one month’s time the plugin’s ratings have dropped from 4.1 to 3.8, but CloudFlare appears to be responsive in the support forums. The company is actively working on rewriting the features that are causing issues.
CloudFlare is installed on more than 100,000 WordPress sites. Users should be prepared to make a backup of their sites before applying this major update.

It is nice to see CLoudflare working on better integration with the WordPress platform. It will be interesting to see how this impacts other such plugin such as WordFence which handles WAF rules for well over a million or more WordPress sites.
As a user of both Cloudflare’s services and WordFence, it means I will have to do that much more investigation to determine which options from each will become more viable on a case by case basis.
Thanks for the great update.