Pippin Willamson, creator of the AffliateWP plugin, has discovered a serious bug within the All In One WordPress Security and Firewall plugin. According to a forum thread created by Williamson, All In One WordPress Security and Firewall automatically detects option ids with fwp as malicious and deletes them.
Known WP Pharma Hack Entry: fwp and option_id: 1101143
The options table entry with known pharma hack for option_id 1101143 with option_name affwp_settings was successfully deleted
The pharma hack was well underway in early 2011 but made headlines in the WordPress community when Chris Pearson, published a detailed guide explaining how to detect and remove the malicious code. Even though fwp is an option id commonly used by the pharma hack, it’s used by legitimate WordPress plugins as well. As Williamson explains, blindly checking for and deleting fwp in the options table is dangerous.
While it is true that sites that have been compromised by the pharma attack do often contain option names with fwp, this is in no way a conclusive test.
Blindly assuming that an option matching fwp is malicious is really pretty poor and not friendly to legitimate settings that are stored in the database that contain any version of fwp.
For example, all of our settings are stored with a prefix of affwp_. That means that every single one of our database options are immediately flagged by your plugin and deleted without question or any additional evidence to support the malicious flag.
The sheer number of plugins that could be negatively impacted by this poor attempt at accurately identifying malicious option rows is staggering. wp is used in a huge number of plugins and is often combined with a letter or word that represents the plugin, so it’s highly likely that other plugins store options that include the letters fwp in their option name.
Although I don’t use AffliateWP, I installed WordPress All In One Security and Firewall on my localhost and used the database scanner to see if any option ids are discovered using fwp. During the database scan, it discovered the option id of sfwpavatar and promptly removed it from the database. Sfwpavatar is related to the Simple Forums plugin, specifically to handle avatar images. The id has nothing to do with the pharma hack.
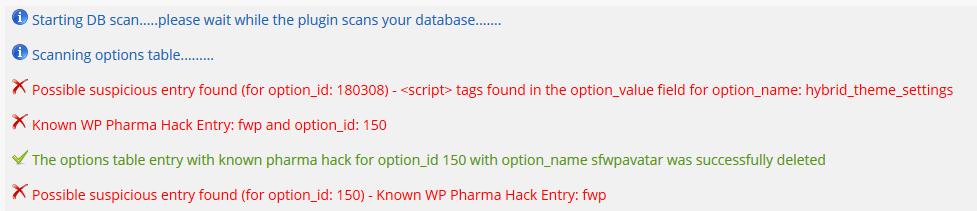
Option 150 as seen in the wp_options table in the database.

I reached out to the developers of the All In One WordPress Security and Firewall plugin to find out when a fix can be expected. At the time of publishing, they have yet to respond. This post will be updated when or if they respond.
Until an update is pushed out that explicitly addresses this bug, I would avoid using it or at the very least, the Database Scanner.
New Version Temporarily Disables Database Scanner
The team has pushed out a new version that addresses the issue discussed in the post. You should already see an update notification in the dashboard. According to the change log, the update temporarily disables the Database Scanner.
Pippin posted that 19 hours ago. Can’t we wait a little bit more until the plugin authors have time to properly respond to that before we make this another public “shame on you” thing? Good lord, what we have become…