Wordfence has published the details of two stored XSS vulnerabilities the company responsibly disclosed to the developers of the All In One SEO plugin in January 2023. The vulnerabilities potentially impacted more than 3 million users on versions 4.2.9 and earlier.
One vulnerability, which received a 6.4 (Medium) CVSS score, Wordfence attributes to insufficient input sanitization and output escaping. Researchers found that this “makes it possible for authenticated attackers with Contributor-level access or higher to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.”
The second vulnerability was given a 4.4 (Medium) CVSS score and requires an authenticated attacker to have Administrator-level privileges. Wordfence outlined how attackers might exploit these vulnerabilities:
Unfortunately, vulnerable versions of this plugin fail to escape submitted site titles, meta descriptions and other elements during post and page creation, and when changing plugin settings. This made it possible for users with access to the post editor, such as contributors, to insert malicious JavaScript into those fields, which would execute in the browser of any authenticated user, such as a site’s administrator, editing such a post or page.
This is a likely scenario to occur as posts written by contributors have to be reviewed and moderated prior to publication.
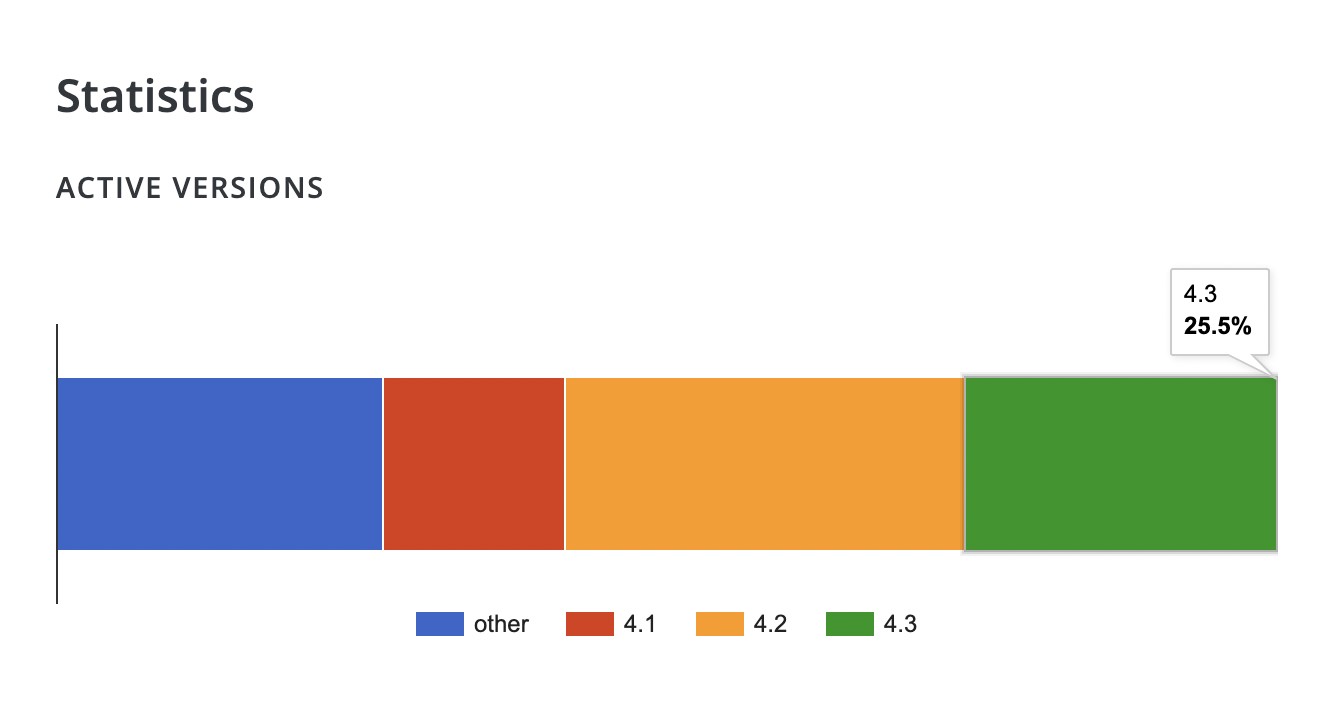
All In One SEO has patched both vulnerabilities in version 4.3.0 but so far only 25.5% of the plugins 3+ million user base has updated to the latest version, leaving approximately 3/4 of the plugin’s users still vulnerable.
The plugin’s changelog for version 4.3.0 includes a brief, vague note on the security fix included: “Updated: Additional security hardening.” There have been two more releases of the plugin since the vulnerabilities were patched in 4.3.0.
The claim that Wordfence responsibly disclosed these isn’t really true, as they indirectly disclosed in the post that they were selling access to information on one of the vulnerabilities a day before they notified the developer (in the form of a firewall rule). So any hacker willing to pay for their Wordfence Premium service got the information before the developer, which isn’t responsible disclosure and seems problematic from a security provider. Hopefully, you will do a follow up post covering that aspect of this.
The other vulnerability isn’t really a vulnerability, since the attacker would already need to have access to a WordPress account with the Administrator role, which already normally has the capability to do the equivalent of the vulnerability.