Last August, Automattic acquired Parka, LLC, the makers of the BruteProtect security tool for WordPress, with the goal of integrating its features into Jetpack. The services provided in BruteProtect Pro were subsequently offered for free.
Jetpack 3.4 was released today with brute force protection available to users via a new module called Protect. You can find it under the Jetpack settings page or within your centralized dashboard on WordPress.com.
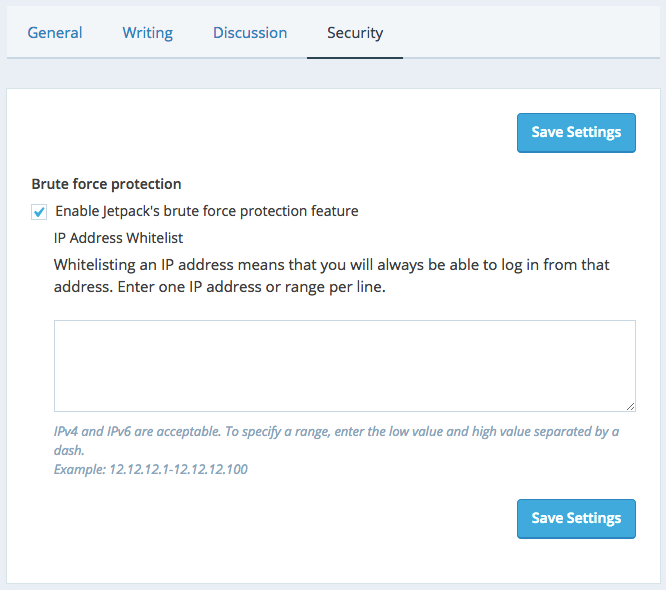
Enabling protection against botnet attacks is as simple as checking a box:
The new module protects your login form from brute force attempts and allows you to scan your site for malicious code in Jetpack. It also allows you to manage a whitelist of IP addresses if you ever need to prevent Jetpack from blocking one.
At the bottom of your Jetpack stats summary, where you find the number of spam comments blocked by Akismet, you’ll also now see the number of blocked malicious login attempts.
As of February 2015, the BruteProtect plugin has defended over 225,000 sites from more than 350 million botnet attacks. The plan is to phase out the independent plugin by the end of 2015 in favor of maintaining its features via Jetpack.
Jetpack Protect is a truly compelling new addition to the plugin. Its inclusion means that millions of WordPress sites will now have free access to protection against brute force attacks, making a large portion of the web more secure.
With the addition of Protect, the plugin has grown to include 36 modules, which can be a bit overwhelming for new users. Jetpack 3.4 introduces a new “Jump Start” feature that will activate a curated set of modules to get you started. This release also includes a list of 43 enhancements and 11 bug fixes, which you can view on the plugin’s changelog.
So now there is brute force attacks functionality, there is a contact form functionality…
Should I delete the brute force plugin I have, same for contact form? What is better for my site?