In a disclosure to the U.S. Securities and Exchange Commission (SEC) that was published today, GoDaddy announced a data security breach impacting its WordPress managed hosting customers. The company discovered unauthorized third-party access to its hosting environment on November 17, 2021, through an exploited vulnerability.
GoDaddy’s initial investigations show the attacker gained access using a compromised password beginning on September 6, 2021. Nearly every sensitive data point associated with hosting a WordPress website was compromised, including customer email addresses, admin passwords, sFTP and database credentials, and SSL private keys. GoDaddy published the following summary of data the attacker had access to for more than two months:
- Up to 1.2 million active and inactive Managed WordPress customers had their email address and customer number exposed. The exposure of email addresses presents risk of phishing attacks.
- The original WordPress Admin password that was set at the time of provisioning was exposed. If those credentials were still in use, we reset those passwords.
- For active customers, sFTP and database usernames and passwords were exposed. We reset both passwords.
- For a subset of active customers, the SSL private key was exposed. We are in the process of issuing and installing new certificates for those customers.
GoDaddy has more than 20 million customers but only the managed WordPress hosting accounts were affected by this breach. Looking further into the incident, Wordfence claims that GoDaddy was storing sFTP credentials as plaintext, although GoDaddy has not officially confirmed it:
GoDaddy stored sFTP passwords in such a way that the plaintext versions of the passwords could be retrieved, rather than storing salted hashes of these passwords, or providing public key authentication, which are both industry best practices.
We confirmed this by accessing the user interface for GoDaddy Managed Hosting and were able to view our own password…When using public-key authentication or salted hashes, it is not possible to view your own password like this because the hosting provider simply does not have it.
GoDaddy’s stock tumbled after the SEC disclosure got picked up by major news organizations, finishing down 5.25%. The company emailed its customers to notify them that their accounts may have been compromised during the two months when the attacker had unauthorized access.
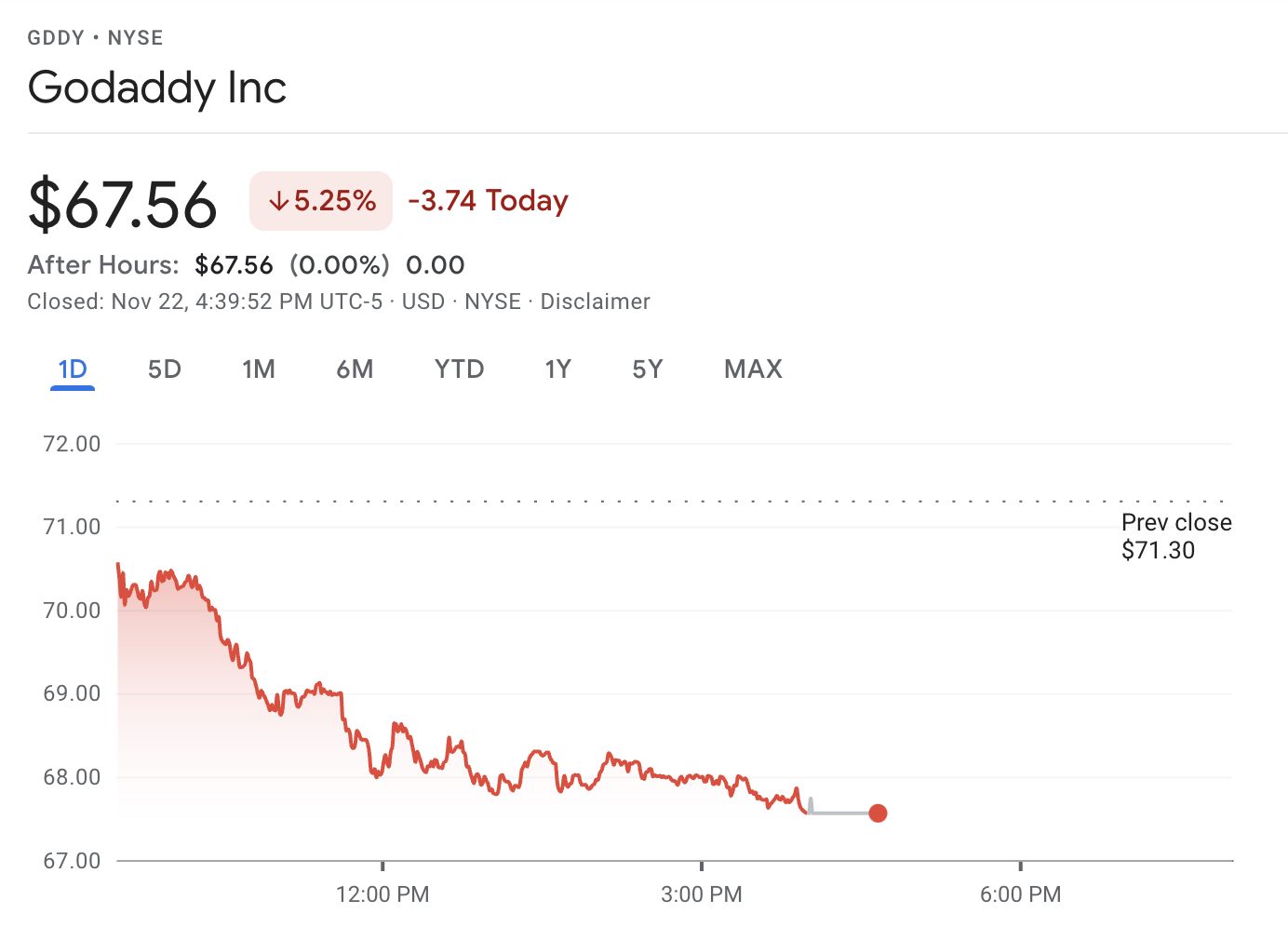
The incident has damaged customers’ trust and puts developers and agencies in an uncomfortable position if they are required to notify their customers about the breach. Impacted site owners will need to watch for malware, suspicious activity, and potential phishing attacks.
Godaddy says it has already taken steps to further secure its provisioning system and is continuing its investigation with the help of an IT forensics firm and law enforcement.
This is really shocking news. I also have blogs hosted on Managed WordPress hosting of Godaddy. Yesterday My WordPress admin password was also compromised and I have changed it. I will definitely move my blogs to new a and reliable hosting provider.
Regards,
Vishwajeet Kumar