WordPress users have been subject to a rash of plugin vulnerabilities over the past couple of months. Some of these vulnerabilities have been so widespread that the FBI recently warned users of attacks designed to exploit WordPress sites.
Not long after WordPress published its Security White Paper, an outbreak of issues popped up, starting with a blind SQL injection vulnerability in WordPress SEO by Yoast, followed by a security release from the Pods Framework, and a few other plugins containing similar issues.
WordPress.org has not yet created a way to publicly identify the plugins for which its security team is pushing out automatic updates. The process involves coordination with the plugin developer and the core developers who have been allocated to verify and test the vulnerabilities.
Once their automatic update process for mitigating serious vulnerabilities is ironed out, it would be helpful to have a section of WordPress.org dedicated to transparency about which plugins have received these forced automatic updates.
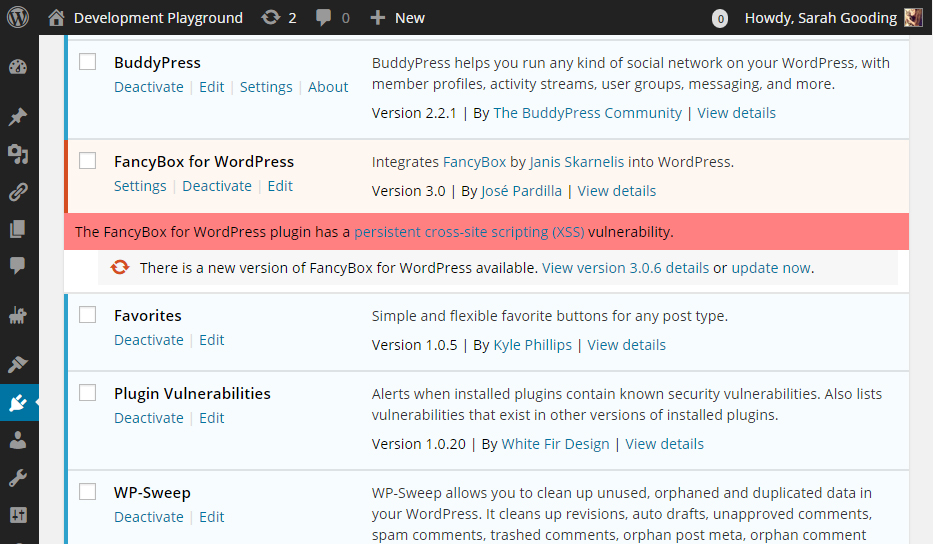
In the meantime, WordPress users need to remain vigilant about staying current with updates. Plugin Vulnerabilities is a plugin that helps users stay on top of security releases. Once installed on your site, it can automatically detect known security vulnerabilities in any of your installed plugins. It will alert you via the admin and you can also turn on email alerts for notification in your inbox.
The plugin was created White Fir Design, a Colorado-based company that specializes in WordPress security and fixing hacked websites. The company also offers a security bug bounty program for WordPress and plugins.
White Fir Design regularly updates the plugin with alerts for new vulnerabilities. The description page gives an overview of the vulnerability stats, as of April 6, 2015:
- 257 vulnerabilities included
- 61 included vulnerabilities are in the most recent version of plugins (57 of these plugins have been removed from the Plugin Directory)
- 24 vulnerabilities have been fixed in part due to this plugin
- 5 included vulnerabilities in security plugins
The top vulnerability types since the creation of the plugin include:
- Cross-site request forgery (CSRF)/cross-site scripting (XSS): 52 vulnerabilities
- Reflected cross-site scripting (XSS): 45 vulnerabilities
- Arbitrary file upload: 45 vulnerabilities
- Arbitrary file viewing: 23 vulnerabilities
- SQL injection: 16 vulnerabilities
The plugin has an admin page listing all vulnerabilities relevant to the plugins you have installed, as well as those that have vulnerabilities in other versions. There will be times when a vulnerability is reported before any update is available, in which case you might want to deactivate and remove the plugin in question.
Updating software for security issues is a natural part of life on the web. With the popularity of WordPress at an all-time high, the discovery of vulnerabilities in core and third party extensions is only going to increase. If you feel overwhelmed by keeping up with security updates, the Plugin Vulnerabilities plugin can help you be more responsive to potential threats.

Good intentions, and it provides valuable functionality. But ultimately it isn’t going to put a dent in the issue. It’s still a plugin that you need to install and activate and the vast majority of WordPress users simply aren’t going to do so. Not only that, but they will have never even known about it.
An issue this large and widespread needs to be addressed within the project itself. At it’s very core.
Nagging people to update is also not the answer. Neither is education because you’re not going to reach everyone that needs to be reached.
One solution that will help is more widespread use of background automatic updates.
That is not a popular idea in some circles of the WordPress development community but i’ve yet to hear anyone that knows of viable solutions to this problem that would have a greater impact or even any real impact at all.
Those developers seem to forget that if it’s not for them they can simply disable it. Because… hooks and filters are cool like that.
I’m beating a dead horse here as i’ve already expressed this opinion numerous times. But issues related to widespread exploitation of vulnerable out of date WordPress installs is not going to go away and will only get worse as WordPress continues to grow in marketshare.