The Google Chrome Security team announced yesterday the browser will begin labeling HTTP connections as insecure starting in January 2017. Chrome currently displays a green lock icon in the address bar for sites that are secure but the security team will be taking it one step further by displaying a warning on unencrypted sites.
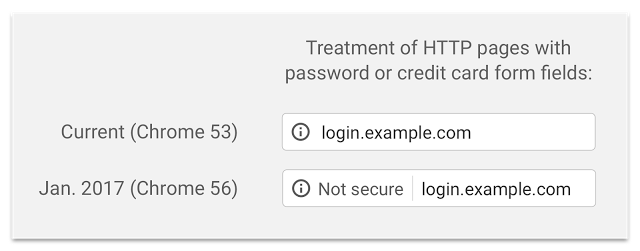
“Beginning in January 2017 (Chrome 56), we’ll mark HTTP sites that transmit passwords or credit cards as non-secure, as part of a long-term plan to mark all HTTP sites as non-secure,” said Chrome Security Team member Emily Schechter. The first step in the plan is to display a “Not secure” label in the address bar:
The announcement cited a study on connection security indicators that showed users do not perceive the lack of a green lock icon as a warning that a site is not secure and can become blind to warnings they see too frequently. The Chrome Security Team used this information to write a plan for changing the browser to clearly display that HTTP sites do not provide data security.
Chrome 56 will be the first release that labels HTTP pages with password or credit card form fields as insecure. Google plans to extend the HTTP warnings to Incognito mode in following releases and will eventually add a prominent red triangle to the label on all HTTP pages.
Site owners who want to avoid having their HTTP sites labeled as not secure have roughly three months to secure their sites. Chrome’s long-term plan to mark HTTP sites as insecure, coupled with the progress the free Let’s Encrypt initiative is making, may help close the gap on the web’s remaining unencrypted sites.
Scare tactics rarely work, and the implication that a site with SSL is secure is just false in any case. I predict that 99% of the users will ignore this like they ignore the mixed content warning that is on many sites that use HTTPS. They will categorize it under “too technical for me to understand” and will keep on with their lives