One of the security tips you’ll come across often is immediately deleting the admin user after installation and creating a new user, then assigning that user the administrator role. This is something I wish the core team would address so that during the installation of WordPress, users would be able to choose their own username and select a strong password without having to go back and delete the initial admin account.
Something New Learned At My WordPress Meetup
While attending my local WordPress meetup, one of the new WordPress users in attendance mentioned the security tip of deleting the administrator account that is created during installation and creating a new user account that is then assigned the administrator role. The idea being that hackers try to login with admin as the username and then try multiple different passwords. I had mentioned that it would be great if WordPress enabled users to make this change during installation instead of having to do it after the fact.
Turns Out You Can
I discovered during a brand new WordPress 3.7 install that users were able to change the default username from admin, to something else. This is the first time I’ve installed WordPress in a long time which is why I didn’t know this change already took place. It also didn’t dawn on me because people are still sharing the security tip I mentioned above. This combination of the enhanced password strength meter and the ability to change the default admin user name during install saves new WordPress installation admins from having to go through a security step that has been preached about for years. As it turns out, users have been able to change the default username of admin for a number of versions. Based on research I conducted, this change has been in place since at least version 3.0.
Why Are We Still Preaching This Security Tip?
With that being the case, why have so many fresh installs decided to use admin as the default username? Why do we continue to preach the security tip of immediately deleting admin and replacing it with a different username? One of the suggestions at my local meetup was to not auto fill the username field with admin and instead, force new installers to create their own unique username. This sounds like a good suggestion to me. When we tried to do a fresh install of WordPress 3.6.1 to see what would happen, admin was automatically filled in for the username. It seems to me that making this simple change would make WordPress installs that much more secure right out of the gate.
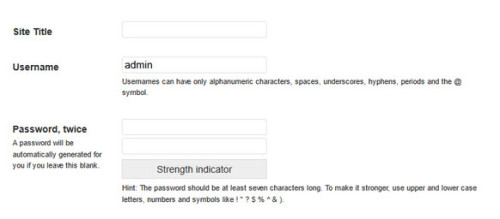
wouldn’t leaving the admin account there, with a long ‘random’ string for a password, but with no permisions granted be more effective – the would be hacker finds ‘admin’ to attack, and isn’t going to get anywhere with it even if he strikes lucky with the password. (Coupled with the wordfence plugin to temporarily lock the ip out so it can’t mount a denial of service attack)
(or does wordpress not give distinct responses for invalid password and invalid username?)