Due to its popularity, WordPress is a favorite target of hackers looking to exploit any vulnerability to gain access to your site. Once inside they can do things like compromise your files, deface your website and start gobbling up all your server’s resources until you are shut down.
With services like BruteProtect gaining traction and the recent widespread brute force attacks on WordPress sites, the incidence of compromised sites appears to be on the rise.
Experts who specialize in reversing hacked WordPress sites will generally tell you that the most important thing you can do is create a strong password. WordPress 3.7’s improved password strength meter came at just the right time. Assuming you’ve already selected a strong password, it’s time to take it one step further with the help of plugins.
WP Admin Graphic Password is a plugin that puts a new twist on WordPress’ traditional authentication mechanism. In addition to entering your text-based username and password, this plugin adds a graphic password for the site administrator.
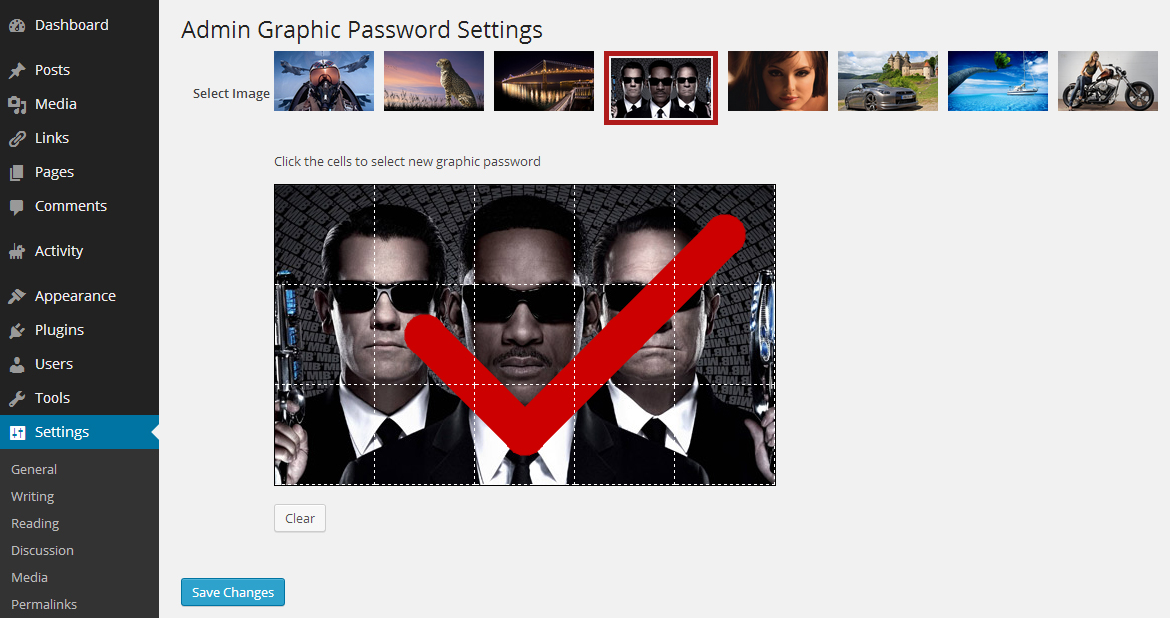
After you install the plugin, the settings page allows you to select an image and then add your password using your mouse or finger, in the case of mobile devices.
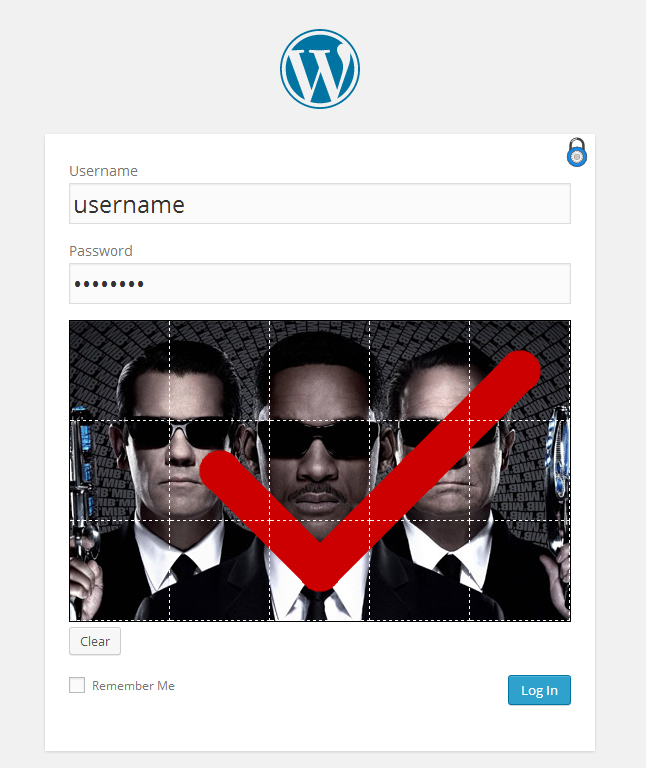
After your password is set, the login page will require your graphic password as well as your original text-based username/password combination. If either one is omitted, you will not be permitted to enter the site. The lock button must be toggled open in order to reveal the graphic password entry, which is a further advantage against bots that are only trained to go after the traditional login form.
The only way to crack this method is if the hacker employs a machine trained on heuristic attacks against graphic password interfaces. This is certainly not as common as attacks on text-based authentication. Combine the two methods and your average nefarious bot is going to have to be smart as hell to get through.
Is this as strong as multi-factor authentication? Probably not. Generally two-factor authentication for WordPress utilizes the “something you have” requirement by asking you to produce a verification code from your phone. If you cannot be bothered with this or simply don’t have your phone on you at all times, then the graphic password might be a good alternative for you.
I tested WP Graphic Admin Password and found it to work as advertised. It is a simple and convenient tool for adding a higher level of security to your WordPress site. It is especially useful if you frequently access your site from a public, possibly infected, computer that might be logging text-based passwords. Download WP Graphic Admin Password for free from WordPress.org.
Update:
The plugin was removed from the repository due security violations but will be back in the WordPress repository after it passes a second review. We’ll update this post when it’s fixed and re-approved.
Wow. This looks like a slick plugin and a great method for adding an extra layer of security.
At first read I was a bit thrown by the need for something like this as I would assume most WordPress Admins always have their phones available for two-factor authorization, but then I remembered the dangers of assuming;)
As WordPress continues to gain popularity around the world and keeps making it’s way to less experienced bloggers and publishers who may not be fortunate enough to even own a mobile phone, this seems like a great option.