![]() Security research firm Sucuri is reporting more than 162,000 WordPress sites were used in a distributed denial of service attack. Compromised machines or websites are generally used to facilitate these types of attacks but in this case, clean WordPress sites were used via XML-RPC.
Security research firm Sucuri is reporting more than 162,000 WordPress sites were used in a distributed denial of service attack. Compromised machines or websites are generally used to facilitate these types of attacks but in this case, clean WordPress sites were used via XML-RPC.
XML-RPC is used in WordPress as an API for third-party clients such as WordPress mobile apps, popular weblog clients like Windows Writer and popular plugins such as Jetpack. XML-RPC is used for pingbacks and trackbacks which are a good thing but can be heavily misused to start DDoS attacks.
Just in the course of a few hours, over 162,000 different and legitimate WordPress sites tried to attack his site. We would likely have detected a lot more sites, but we decided we had seen enough and blocked the requests at the edge firewall, mostly to avoid filling the logs with junk.
One attacker can use thousands of popular and clean WordPress sites to perform their DDoS attack, while being hidden in the shadows, and that all happens with a simple ping back request to the XML-RPC file.
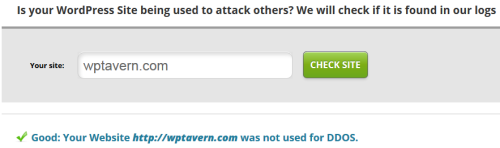
To see if your site was misused, Sucuri has a DDoS scanner available. Enter your domain into the field provided and the scanner will try to locate it within their log files. If the domain doesn’t show up, you know the site wasn’t used to attack others. Thankfully, WPTavern was not used to attack any other websites.
Not As Easy As Turning Off XML-RPC
Unfortunately, disabling XML-RPC presents more problems than solutions. Jetpack uses it to authenticate with WordPress.com and then uses it after the fact to communicate with the Jetpack powered site. It would also disable the ability to use any of the WordPress mobile apps to communicate with the site.
Automattic employee Alex Shiels, responded in the comments of the article that they’ve identified the source of the pingbacks, and are looking to see if the Akismet plugin can help to prevent it. He also mentioned on Twitter the security team is working on a solution.
https://twitter.com/tellyworth/status/443212073967685632
How To Disable Only Pingbacks
While Sucuri has a code snippet you can add to turn off only the pingback functionality of XML-RPC, I was told it will severely effect WordPress sites running on PHP 5.2 due to using an anonymous function. The following code snippet will work correctly without any adverse effects. It disables pingbacks while allowing things like Jetpack and WordPress mobile apps to function normally. Add the code to your theme’s functions.php file.
[php]
add_filter( ‘xmlrpc_methods’, ‘remove_xmlrpc_pingback_ping’ );
function remove_xmlrpc_pingback_ping( $methods ) {
unset( $methods[‘pingback.ping’] );
return $methods;
} ;
[/php]
Is It Time For Pingbacks and Trackbacks To Go?
WPTavern is no stranger to denial of service attacks due to pingbacks and trackbacks. In 2010, I explained how WPTavern was trackbacked to death. Shortly after the website came back online, I disabled both as I feared they might end up taking the site down again. A few years have gone by and I’ve re-enabled pingbacks and trackbacks with no ill effects. However, I wonder if it’s time to kill them once and for all, not just on WPTavern but in WordPress in general.
I liked the old solution where XML-RPC was disabled by default and users had an option to turn it on as needed.
Would be curious to know what percentage of WordPress users actually use the WordPress mobile app.