
Wouldn’t it be nice if there was an equally easy way to tell if WordPress files had been tampered with or hacked? For the average user or developer, it’s not easy to assess core files and plugins for tampering.
Over the past few days I’ve been following a discussion on wp-hackers regarding tools that can detect file tampering. WordPress developers shared a few of their favorite methods of detection and repair.
Quick Diagnostic Tools
If you suspect that your site has been compromised, there are a few free tools that will perform a cursory diagnostic for you. First, you might consider visiting Google’s Safe Browsing diagnostic tool. Enter your URL at the end of this link:
http://www.google.com/safebrowsing/diagnostic?site=wptavern.com
Although it doesn’t let you know if WordPress core file have changed, you can get a general idea if your site has been distributing malware. This tool will let you know the following
- If your site’s current listing status is suspicious
- If Google found that malicious software being downloaded and installed without user consent when visiting your site
- If the site has acted as an intermediary resulting in further distribution of malware
- If your site has hosted malicious software over the past 90 days
The Sucuri SiteCheck remote scanner is another free diagnostic tool that can quickly check blacklisting, malware, malicious javascript, malicious iFrames, drive-by downloads, anomalies, IE-only attacks, suspicious redirections and spam.
Of course, there are plenty of things that Sucuri and Google cannot detect, so don’t stop there. If you want to get into the nitty gritty of tracking down WordPress files that have been hacked, you’ll want to employ a WordPress-specific tool.
Free WordPress Plugins to Detect File Tampering
Several free plugins stand out as excellent options for performing quick scans on WordPress installations. Beyond those there are also some great options for continually monitoring your WordPress site for file tampering.
Exploit Scanner
 The Exploit Scanner plugin was created by developer Donncha O Caoimh to search both the files and the database of your website for signs of suspicious activity. It can also detect unusual file names among your list of active plugins.
The Exploit Scanner plugin was created by developer Donncha O Caoimh to search both the files and the database of your website for signs of suspicious activity. It can also detect unusual file names among your list of active plugins.
Results will indicate helpful notes, more serious warnings or severe threats. The plugin is, however, simply a diagnostic tool. Once you discover something, you’ll need to remove the threat manually.
Sucuri Security – SiteCheck Malware Scanner
 The folks at Sucuri have created a free plugin for WordPress sites that performs a wide range of security checks. Sucuri SiteCheck Malware Scanner should provide you with a decent indication of whether or not your site has been compromised. The plugin is able to detect various types of malware, SPAM injections, website errors, disabled sites, database connection issues, code anomalies and much more.
The folks at Sucuri have created a free plugin for WordPress sites that performs a wide range of security checks. Sucuri SiteCheck Malware Scanner should provide you with a decent indication of whether or not your site has been compromised. The plugin is able to detect various types of malware, SPAM injections, website errors, disabled sites, database connection issues, code anomalies and much more.
In addition to its detection features, the Sucuri scanner is also able to automatically perform a number of measures to harden your WordPress install, including:
- Verify WordPress Version
- Protect Uploads Directory
- Restrict wp-content Access
- Restrict wp-includes Access
- Verify PHP Version
- Disable the theme and plugin editors
- Scan all WordPress core files for changes
Lastly, the Sucuri Scanner’s “Post Hack” feature is very useful for a site that may have been compromised. It allows you to automatically reset all passwords and secret keys for all users on the installation.
Free WordPress Plugins For Actively Monitoring File Tampering
If you want to actively monitor your WordPress site for file tampering, there are a couple of excellent plugins that will help you.
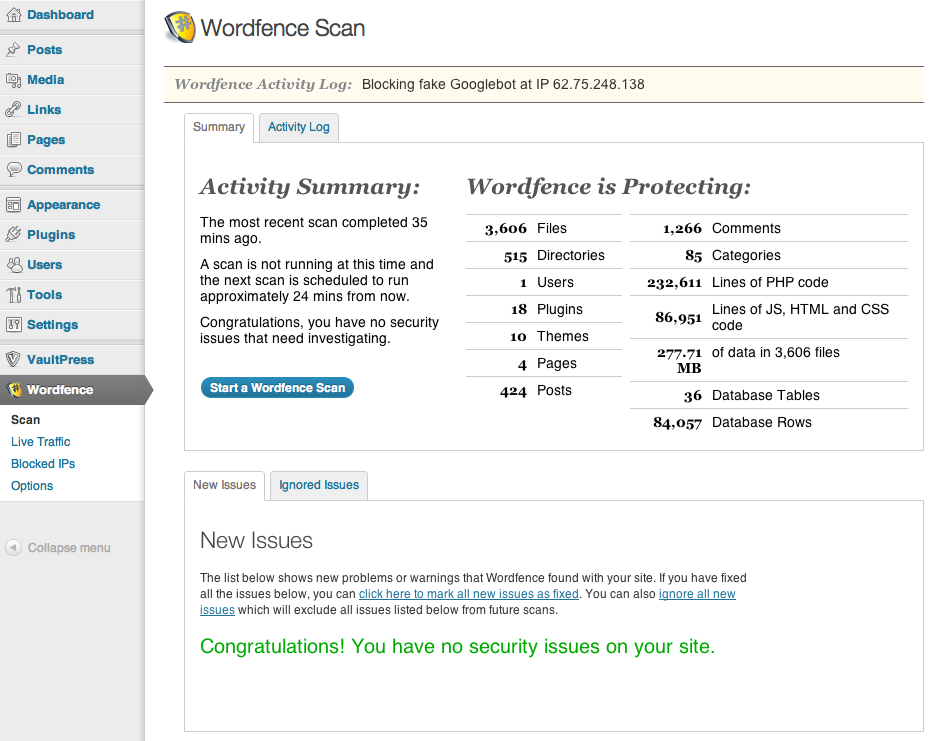
Wordfence Security
Wordfence Security is a plugin that scans core files, themes and plugins against WordPress.org repository versions to check their integrity. The plugin continuously scans for malware and phishing URLs, including all URLs on the Google Safe Browsing List. It checks all your comments, posts and files to find security threats. Wordfence is also multisite-compatible and you can run the security scan for every blog on your network with one click. You can also elect to repair tampered files automatically.
In addition to scanning files for integrity, the plugin also provides a host of other security features to help keep your site safe from compromise. Some of the highlights include:
- Monitors disk space (Many DDoS attacks attempt to consume all disk space to create denial of service)
- Ability to implement Two Factor Authentication
- Option to enforce strong passwords for your administrators, publishers and users
- Includes a firewall to block common security threats like fake Googlebots, malicious scans from hackers and botnets
- Scans for old versions of timthumb script
Wordfence has dozens of configurable options but if you need more you can purchase a Premium API key that gives you Cellphone Sign-in via SMS, lets you block countries and schedule scans for specific times.
WordPress File Monitor Plus
Another excellent plugin to detect file tampering is WordPress File Monitor Plus. This plugin continuously monitors your WordPress site for added/deleted/changed files. When a change is detected, it will send you an email alert. In case you didn’t receive the email, you’ll also receive alerts within the WordPress admin area.
WordPress File Monitor Plus is also multisite-compatible. Its main features include:
- Ability to monitor files for changes based on file hash, time stamp and/or file size
- Ability to exclude files and directories from scan (for instance if you use a caching system that stores its files within the monitored zone)
- Site URL included in notification email in case plugin is in use on multiple sites
- Ability to run the file checking via an external cron so not to slow down visits to your website and to give greater flexibility over scheduling
- Ability to set file extension to be ignored or only scanned
The huge advantage of having a plugin like this in place is that you don’t have to remember to perform regular scans. It’s like having an extra set of eyes on your site at all times. You’ll receive alerts in your inbox if anything suspicious is detected.
What to Do if You’ve Been Hacked
It’s important to find out whether you have plugin, theme or core files hacked. If you’re not using a plugin that automatically performs repairs, then you’ll need to figure out which files need to be replaced. If the threat ends up being within core files, there’s not much use in tracking down the exact file. You might as well replace them all. A manual re-installation of WordPress is in order. Make backups before starting any repairs for hacked files. Also, remember to check your .htaccess file for changes that may have been added without your knowledge.
WordPress has long been a special target of hackers and spammers alike. The codex has a lengthy resource for how to clean up a site that has been hacked and tips for Hardening WordPress. Old, unprotected WordPress sites are especially vulnerable. One of the best things you can do to help keep your site secure is to make sure it’s updated to WordPress 3.7, which offers background updates for security and minor releases.

That’s a great post and I’ve been using these plugins on most of my sites (in addition to some alternatives of the Exploit Scanner).
My favorite one is definitely the WordPress File Monitor, as most of the hacked sites I’m dealing with are due to hacked account on a shared hosting or a plugin vulnerability that allows for shell upload, or anything like that. Catching that break in an early stage allows you to take actions and prevent future issues, and rewind through the logs and see how/when it happen exactly.